Many security breaches start internally

For the 17th consecutive year, Verizon Business publishes its annual and comprehensive IT security study: the Data Breach Investigations Report (DBIR). The report analyzed 8,302 security incidents in Europe, the Middle East and Africa (EMEA), of which 6,005 (more than 72 percent) were confirmed IT security breaches.

Nearly half of all breaches (49 percent) begin internally, indicating a high level of abuse of privilege and human error. The main causes of cyber security incidents are various types of errors, system intrusions and social engineering, which account for 87 percent of all breaches. The most common categories of information compromised are personal data (64 percent), internal data (33 percent), and ID information (20 percent).
The human element remains the front door for the cybercriminals
Most IT security breaches globally (68 percent), regardless of whether they involve a third party or not, involve so-called non-malicious human actions, i.e. people who make mistakes or who fall victim to social engineering, where fraudsters manipulate their victims in order to gain access to confidential data.
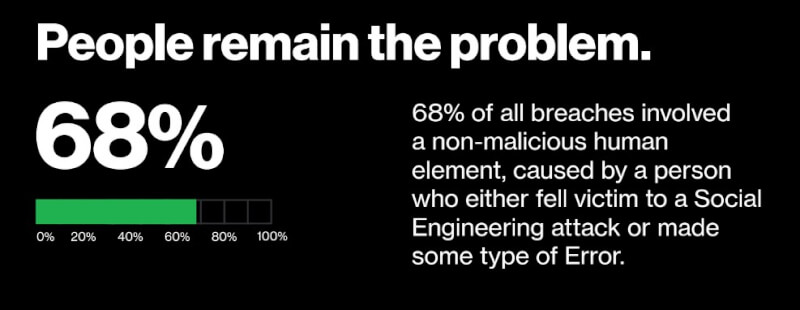
This percentage is about the same as last year. A potentially opposite trend is the improvement in reporting methods: 20 percent of users both identified and reported phishing in simulation efforts, while 11 percent of users who clicked on the email also reported it.

"The fact that the human element continues to play such a large role in breaches of IT security shows us that companies in Europe must maintain their focus on prioritizing education and on increasing knowledge of the best practices in cyber security. The increase in the reporting that we are seeing is promising and indicates a cultural shift among employees in the view of how important it is to be aware of cyber security,” says Sanjiv Gossain, EMEA Vice President, Verizon Business.
Zero day vulnerabilities are a continuing threat to businesses
Globally, the use of vulnerabilities to initiate breaches of data security has increased in the past year and accounts for 14 percent of all breaches. This increase was primarily driven by the scale and growing frequency of zero day exploits by ransomware actors, in particular the vulnerability in the file transfer program MOVEit has been a widespread exploit of a zero day vulnerability.
"Ransomware actors' exploitation of zero-day vulnerabilities is a continuing threat to businesses, not least because of the interconnected supply chains," said Alistair Neil, EMEA Senior Director of Security, Verizon Business "Over the past year, 15 percent of all breaches involving a third party, including vulnerabilities in third party software as well as other direct or indirect supply chain issues."
Analysis of the Cybersecurity Infrastructure and Security Agency's (CISA) Known Exploited Vulnerabilities (KEV) catalog showed that, on average, it takes companies 55 days to remediate 50 percent of critical vulnerabilities after patches become available. At the same time, the median time to detect a large exploit CISA KEV vulnerabilities on the Internet is five days.
As a possible consolation, artificial intelligence (AI) has proven to be less of a culprit than feared when it comes to large-scale vulnerabilities:
"While the use of artificial intelligence to gain access to valuable enterprise assets is a concern going forward, the inability to patch and close basic vulnerabilities means that threat actors need not rush to focus on accelerating the use of social engineering," says Chris Novak, Sr. Director of Cybersecurity Consulting, Verizon Business.
Other key findings
About 32 percent of all breaches involved some form of extortion technique, including ransomware.

Over the past two years, about a quarter (between 24 and 25 percent) of financially motivated security incidents involved pretexting, where people are tricked into sharing confidential information.
Over the past 10 years, the use of stolen ID information has occurred in nearly a third (31 percent) of all IT security breaches.
Latest software
-
28 Augsoftware
-
07 Augsoftware
Musk is suing OpenAI for focusing on profit
-
07 Augsoftware
OpenAI says goodbye to top managers
-
01 Augsoftware
Google AI systems achieve breakthroughs in mathema
-
29 Julsoftware
AMD Amuse: New AI graphics tool for Ryzen and Rade
-
26 Julsoftware
Logitech G announces MIXLINE
-
28 Junsoftware
Chinese AI company trains LLMs at Huawei
-
26 Junsoftware
ChatGPT desktop app for Mac is ready
Most read software
Latest software
-
28 Augsoftware
Google Meet's new AI feature takes notes
-
07 Augsoftware
Musk is suing OpenAI for focusing on profit
-
07 Augsoftware
OpenAI says goodbye to top managers
-
01 Augsoftware
Google AI systems achieve breakthroughs in mathema
-
29 Julsoftware
AMD Amuse: New AI graphics tool for Ryzen and Rade
-
26 Julsoftware
Logitech G announces MIXLINE
-
28 Junsoftware
Chinese AI company trains LLMs at Huawei
-
26 Junsoftware
ChatGPT desktop app for Mac is ready






