Olympus: Work from Home with Dictation

Sponsored content: This article has been authored in collaboration with Olympus.
For many years, Olympus has been a manufacturer of dictation devices for both private consumers as well as for professionals working in hospitals, law firms, insurance companies and many other types of businesses that might have a need for documenting information in an efficient and safe way.
Store and share memos in a safe place
Being able to work on a set of files with colleagues either close to you, or from afar, maybe even from a different country, is a key aspect in securing an efficient and functional workflow. If, for instance, you are working in an office, your company is likely to have a shared drive that gives its users access to sharing information and files across the entire organization, and between different departments.
Remember GDPR

If you work with law, health care or basically any other line of work where you handle sensitive information, you surely are familiar with GDPR already.
With dictation devices, it’s also important that you, throughout the whole process, are able to protect and keep secure the files that you create. This is achievable with a dictation device that offers encryption, secure file transfer and sharing as well as storage on a secure server.
Storage in the cloud
![]()
When a large number of employees are not physically present at the office, but instead are working from a remote location, such as their home office, this secure process is significantly challenged. Here, a cloud-based approach like Google Drive, Microsoft 365 and OneDrive, with its online storage solution, will make it much easier to share documents between a group of people.
Cloud storage has gained a lot of ground in recent years because it is an ideal and easy way of working across various platforms and it removes the need of endless mail attachments and the use of physical devices such as USB keys.
Beware of security holes
When working from outside of the internal company network, one must be cautious and mindful of the risks that this entails. If, for instance, you are working from home and using your own private computer instead of the one that you would normally use at the office, then neither you nor your company can be sure that the data that you are working on is secured to the same degree as on your company’s internal network. If you use a shared drive on the network, we highly recommend that you as a minimum use a VPN connection to the company server so that your connection is encrypted and thereby harder to “listen” to.
Extra protection
In order to increase security even further, we also recommend the use of two-factor authentication. This could be Google’s Authenticator in combination with a strong password.
You might already know of this feature from shopping online where you receive an SMS with an extra password that you are required to input whenever you use your credit card. In addition, you’ll be given an extra level of protection of the login that you are using in relation to your work. Should your login credential somehow have been compromised, then the unauthorized users will not be able to make it all the way since the SMS or authentication code will be sent to your device.
Two-factor authentication
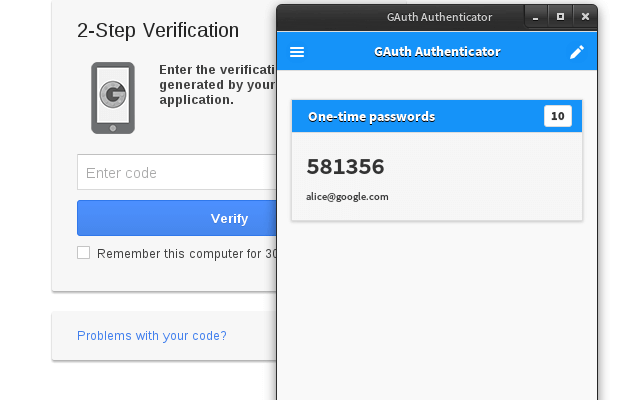
Google Authenticator is an app on your smartphone that provides additional security in the shape of two-factor authentication. It’s like having a secret list of code that you store separately from your PC so that it cannot be compromised and copied. On top of that, the codes provided by Google Authenticator are rotated and updated dynamically.
Secure storage of passwords
It can be tempting to simply hit the “Yes” option whenever your browser asks to store your login credentials when logging in to e.g. Facebook. You save the hassle the next time around, after all. The problem is that the login details are stored locally, and if your laptop is stolen at a time that it is not locked, then a thief can quickly gain access to your most sensitive files and information. Even if you are quick to update the passwords to all the sites and services that you frequent, you’ll be left with that unnerving feeling that you’ve forgotten something.

With a password manager, such as LastPass, your passwords are not stored locally on your computer, but instead securely in the cloud. LastPass is a plugin for your internet browser that will make your login information easily available as soon as you visit a site that it recognizes. The smart thing is that should unauthorized individuals gain access to your computer, then they won’t be able to abuse any of your accounts since your browser won’t be storing your logins and you are required to input a master password in order to access the LastPass vault.
LastPass of course also supports the use of two-factor authentication, so this way you have several layers of security.
Secure dictation
As mentioned, you also have to consider security from beginning till end in real-world scenarios. In terms of dictation, Olympus offers professional solutions that ensure GDPR compliance.
Olympus DS-9000 and Olympus DS-9500 are both dictaphones that can be locked with a PIN code and by using Olympus’s proprietary DSS-format, one’s recordings can be stored with 256-bit AES encryption. This means that if you were to lose your dictaphone, your files will be lost, but at least not compromised. Others won’t be able to access them.

Optimize the security when working offline
Due to the changes that are happening in our society, IT departments are under more pressure than ever. Therefore, Olympus has asked us to share its message on how customers can secure and optimize their daily workflow. If you want to learn more, check out this simple guide.
Source and image credit:
LastPass, Google, Macworld, ZDNet, Olympus
Latest computer
-
04 Seplaptop
-
28 Augtablets
Could the iPad Mini 7 be just around the corner?
-
26 Auglaptop
Coming soon: Samsung Galaxy Book 5 Pro 360
-
08 Augcomputer
HP moves PC production from China
-
05 Auglaptop
Razer Blade 18 (2024)
-
06 Jultablets
Apple iPad 9th Gen
-
05 Jullaptop
AMD Ryzen AI 7 PRO 160 CPU leak
-
27 Junlaptop
The Snapdragon X Plus has serious battery issues
Most read computer
Latest computer
-
04 Seplaptop
Samsung presents first AI laptop
-
28 Augtablets
Could the iPad Mini 7 be just around the corner?
-
26 Auglaptop
Coming soon: Samsung Galaxy Book 5 Pro 360
-
08 Augcomputer
HP moves PC production from China
-
05 Auglaptop
Razer Blade 18 (2024)
-
06 Jultablets
Apple iPad 9th Gen
-
05 Jullaptop
AMD Ryzen AI 7 PRO 160 CPU leak
-
27 Junlaptop
The Snapdragon X Plus has serious battery issues






